Creating elliptic curve public private key with openSSL
TLDR;
# validates secp256k1 ( The curve function bitcoin uses ) is present
openssl ecparam -list_curves | grep secp256k1
# outputs a spec file we will use to generate public/private ec keys
openssl ecparam -name secp256k1 -out secp256k1-spec.pem
# generate ec-private key
openssl ecparam -in secp256k1-spec.pem -genkey -noout -out ec-private.pem
# convert from ec format to pkcs8 format
openssl pkcs8 -topk8 -nocrypt -in ./ec-private.pem -out ./private.pem
# generate public key
openssl ec -in ./private.pem -pubout -out ./public.pem
This is a short blog on generating public/private key pairs using elliptic curves (ec) I use JWT’s to secure the web applications I create. Luckily the library I use also supports ec private/public keys.
alg: "ES256K"Thus I obtain same level of security with fever bits ( compared to RSA ). In order to generate the keys we need to have openssl installed. I prefer to use secp256k1 curve to generate the keys. however openssl supports so much more, the process is same just pick one you like to use.
First verify the openssl has the secp256k1 ec:
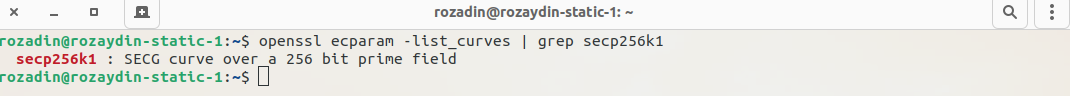
And after that, we will output the parameters of the curve, we will use this file as input to generate private and public keys.
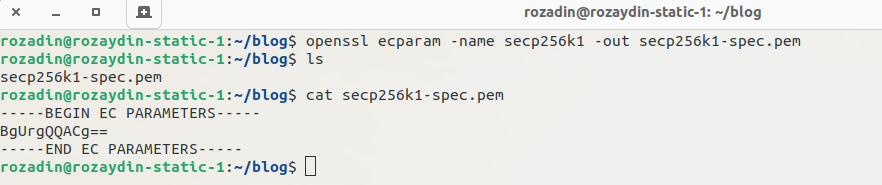
Now creating the private key ( in ec format ):
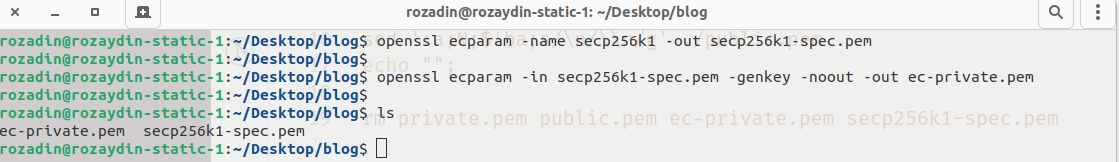
Converting private key into pkcs8 format:
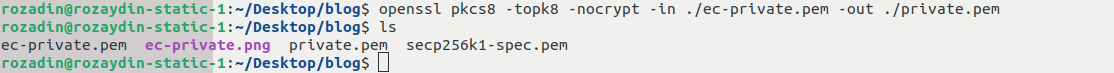
And finally the public key:
All combined in a shell script would be:
#!/bin/bash
openssl ecparam -name secp256k1 -out secp256k1-spec.pem
openssl ecparam -in secp256k1-spec.pem -genkey -noout -out ec-private.pem
openssl pkcs8 -topk8 -nocrypt -in ./ec-private.pem -out ./private.pem
openssl ec -in ./private.pem -pubout -out ./public.pem
echo "";
cat ./private.pem;
echo "";
sed ':a;N;$!ba;s/\n/\\n/g' ./private.pem
echo "";
cat ./public.pem;
echo "";
sed ':a;N;$!ba;s/\n/\\n/g' ./public.pem
echo "";
rm private.pem public.pem ec-private.pem secp256k1-spec.pemThe script display public and private keys in two formats one in a single line (new lines are encoded with \n) and in as is format.
The keys will be in pkcs8 format. Thanks for reading.